Malicious VS Code Extensions With 1.5 Million Installs Steal Developer Source Code
2 Sources
2 Sources
[1]
Malicious VS Code AI Extensions with 1.5 Million Installs Steal Developer Source Code
Cybersecurity researchers have discovered two malicious Microsoft Visual Studio Code (VS Code) extensions that are advertised as artificial intelligence (AI)-powered coding assistants, but also harbor covert functionality to siphon developer data to China-based servers. The extensions, which have 1.5 million combined installs and are still available for download from the official Visual Studio Marketplace, are listed below - * ChatGPT - 中文版 (ID: whensunset.chatgpt-china) - 1,340,869 installs * ChatGPT - ChatMoss(CodeMoss)(ID: zhukunpeng.chat-moss) - 151,751 installs Koi Security said the extensions are functional and work as expected, but they also capture every file being opened and every source code modification to servers located in China without users' knowledge or consent. The campaign has been codenamed MaliciousCorgi. "Both contain identical malicious code -- the same spyware infrastructure running under different publisher names," security researcher Tuval Admoni said. What makes the activity particularly dangerous is that the extensions work exactly as advertised, providing autocomplete suggestions and explaining coding errors, thereby avoiding raising any red flags and lowering the users' suspicion. At the same time, the embedded malicious code is designed to read all of the contents of every file being opened, encode it in Base64 format, and send it to a server located in China ("aihao123[.]cn"). The process is triggered for every edit. The extensions also incorporate a real-time monitoring feature that can be remotely triggered by the server, causing up to 50 files in the workspace to be exfiltrated. Also present in the extension's web view is a hidden zero-pixel iframe that loads four commercial analytics software development kits (SDKs) to fingerprint the devices and create extensive user profiles. The four SDKs used are Zhuge.io, GrowingIO, TalkingData, and Baidu Analytics, all of which are major data analytics platforms based in China. PackageGate Flaws Affect JavaScript Package Managers The disclosure comes as the supply chain security company said it identified six zero-day vulnerabilities in JavaScript package managers like npm, pnpm, vlt, and Bun that could be exploited to defeat security controls put in place to skip the automatic execution of lifecycle scripts during package installation. The flaws have been collectively named PackageGate. Defenses such as disabling lifecycle scripts ("--ignore-scripts") and committing lockfiles ("package-lock.json") have become crucial mechanisms to confronting supply chain attacks, especially in the aftermath of Shai-Hulud, which leverages postinstall scripts to spread in a worm-like manner to hijack npm tokens and publish malicious versions of the packages to the registry. However, Koi found that it's possible to bypass script execution and lockfile integrity checks in the four package managers. Following responsible disclosure, the issues have been addressed in pnpm (version 10.26.0), vlt (version 1.0.0-rc.10), and Bun (version 1.3.5). Pnpm is tracking the two vulnerabilities as CVE-2025-69264 (CVSS score: 8.8) and CVE-2025-69263 (CVSS score: 7.5). Npm, however, has opted not to fix the vulnerability, stating "users are responsible for vetting the content of packages that they choose to install." The Hacker News has reached out to npm/GitHub for further comment, and we will update the story if we hear back. "The standard advice, disable scripts and commit your lockfiles, is still worth following," security researcher Oren Yomtov said. "But it's not the complete picture. Until PackageGate is fully addressed, organizations need to make their own informed choices about risk."
[2]
Malicious Microsoft VSCode AI extensions might have hit over 1.5 million users
* Two VSCode extensions exfiltrated sensitive user data to Chinese servers * ChatGPT - 中文版 and ChatMoss had over 1.5 million installs combined * Extensions used hidden iframes, commands, and SDKs to steal files and track activity More than 1.5 million people may have had their sensitive data exfiltrated to Chinese hackers through two malicious extensions found on the VSCode Marketplace. Security researchers at Koi Security said they discovered two malicious browser extensions in Microsoft's Visual Studio Code (VSCode) Marketplace, the official Microsoft store for code editor add-ons. The extensions were advertised as AI-based coding assistants. Indeed, they worked as advertised, providing users with a simple and convenient way to access a Generative Artificial Intelligence (GenAI) tool to help with coding. However, the tools were also uploading sensitive data to a third-party server in China without telling the users about it. MaliciousCorgi According to Koi, these are the add-ons in question, which are both still available for download on the marketplace : ChatGPT - 中文版 (publisher: WhenSunset, 1.34 million installs) ChatMoss (CodeMoss) (publisher: zhukunpeng, 150k installs) Koi says both are part of the 'MaliciousCorgi' campaign, and both were sending the stolen data to the same server. To exfiltrate the data, they used three distinct mechanisms, it was said. The first one is via real-time monitoring of files opened in VS Code client. As soon as the victim opens a file, its contents are encoded in Base64 and relayed to the servers. "The moment you open any file - not interact with it, just open it - the extension reads its entire contents, encodes it as Base64, and sends it to a webview containing a hidden tracking iframe. Not 20 lines. The entire file," the researchers explained. The second mechanism is a server-controlled command that stealthily sends up to 50 files from the victim's workspace, while the third one is a zero-pixel iframe in the extension's webview where commercial analytics SDKs are loaded. These SDKs track user behavior, build identity profiles, and monitor other activity. Microsoft told BleepingComputer it was looking into the situation, but the add-ons are still available for download. Via BleepingComputer Follow TechRadar on Google News and add us as a preferred source to get our expert news, reviews, and opinion in your feeds. Make sure to click the Follow button! And of course you can also follow TechRadar on TikTok for news, reviews, unboxings in video form, and get regular updates from us on WhatsApp too.
Share
Share
Copy Link
Cybersecurity researchers uncovered two malicious VS Code extensions disguised as AI-powered coding assistants that secretly exfiltrated developer source code to China-based servers. ChatGPT - 中文版 and ChatMoss, with 1.5 million combined installs, remain available on the Visual Studio Marketplace despite actively stealing files and tracking user behavior through hidden mechanisms.
Malicious VS Code Extensions Expose Developer Source Code to Chinese Servers
Cybersecurity researchers at Koi Security have identified two malicious VS Code extensions that masquerade as AI-powered coding assistants while secretly exfiltrating developer source code to servers in China
1
. The extensions—ChatGPT - 中文版 with 1,340,869 installs and ChatMoss (CodeMoss) with 151,751 installs—remain available for download from the official Visual Studio Marketplace despite their malicious activity1
. This discovery matters significantly for developers worldwide who rely on VS Code extensions to enhance productivity, as the tools function exactly as advertised while simultaneously conducting surveillance operations.
Source: Hacker News
MaliciousCorgi Campaign Operates Through Three Distinct Data Exfiltration Methods
The MaliciousCorgi campaign employs sophisticated techniques to siphon developer source code without raising suspicion
2
. Security researcher Tuval Admoni from Koi Security noted that both extensions contain identical malicious code running under different publisher names1
. The first mechanism activates the moment a user opens any file in VS Code, reading the entire contents, encoding it in Base64 format, and transmitting it to aihao123[.]cn, a server located in China1
. This process triggers for every edit, creating continuous data exfiltration as developers work.
Source: TechRadar
The second method involves real-time monitoring that can be remotely activated by the server, enabling the extraction of up to 50 files from the workspace
1
. The third mechanism deploys hidden iframes—zero-pixel iframes embedded in the extension's web view that load four commercial analytics SDKs: Zhuge.io, GrowingIO, TalkingData, and Baidu Analytics1
. These analytics SDKs enable device fingerprinting and create extensive user profiles for user behavior tracking2
.Functional Extensions Lower Developer Suspicion While Stealing Sensitive Data
What makes these malicious Microsoft VSCode AI extensions particularly dangerous is their legitimate functionality. Both tools provide autocomplete suggestions and explain coding errors as promised, effectively avoiding detection while exfiltrated sensitive user data flows to servers in China
1
2
. This dual-purpose design means developers receive genuine value from the extensions while unknowingly exposing proprietary code, intellectual property, and potentially sensitive client information. Microsoft told BleepingComputer it was investigating the situation, but the extensions remained available for download at the time of reporting.Related Stories
PackageGate Flaws Compound Supply Chain Security Concerns
Koi Security also disclosed six zero-day vulnerabilities in JavaScript package managers including npm, pnpm, vlt, and Bun, collectively named PackageGate Flaws
1
. These vulnerabilities allow attackers to bypass security controls designed to prevent automatic execution of lifecycle scripts during package installation, undermining defenses against supply chain attacks1
. While pnpm addressed the issues in version 10.26.0 (tracking them as CVE-2025-69264 with a CVSS score of 8.8 and CVE-2025-69263 with a CVSS score of 7.5), vlt patched in version 1.0.0-rc.10, and Bun fixed them in version 1.3.5, npm declined to address the vulnerability1
. Security researcher Oren Yomtov cautioned that "until PackageGate is fully addressed, organizations need to make their own informed choices about risk"1
. Developers should watch for Visual Studio Marketplace policy changes and consider implementing additional vetting processes for extensions, particularly those offering AI assistance, as the intersection of convenience and security continues to present challenges in the development ecosystem.🟡 untrained:References
Summarized by
Navi
[1]
Related Stories
Two Chrome Extensions Caught Stealing AI Chats from 900,000 ChatGPT and DeepSeek Users
07 Jan 2026•Technology
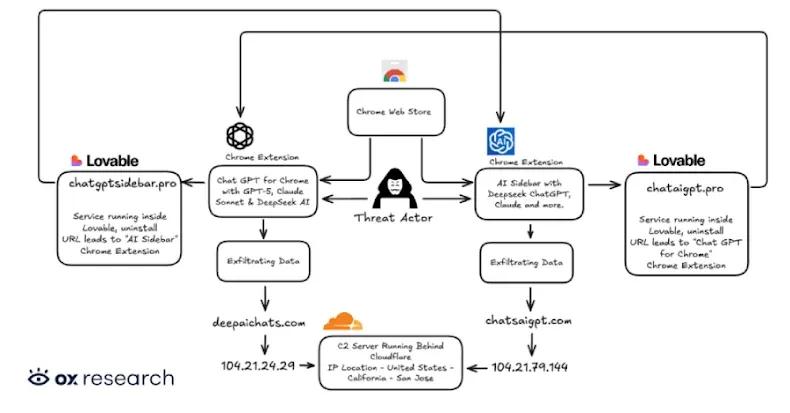
Malicious Chrome extensions disguised as AI assistants steal data from 300,000+ users
12 Feb 2026•Technology

Browser extensions with 8 million users caught secretly harvesting AI conversations
17 Dec 2025•Technology

Recent Highlights
1
ByteDance's Seedance 2.0 AI video generator triggers copyright infringement battle with Hollywood
Policy and Regulation

2
Demis Hassabis predicts AGI in 5-8 years, sees new golden era transforming medicine and science
Technology

3
Nvidia and Meta forge massive chip deal as computing power demands reshape AI infrastructure
Technology





