Popular Chrome VPN Extension Caught Secretly Spying on Users
3 Sources
3 Sources
[1]
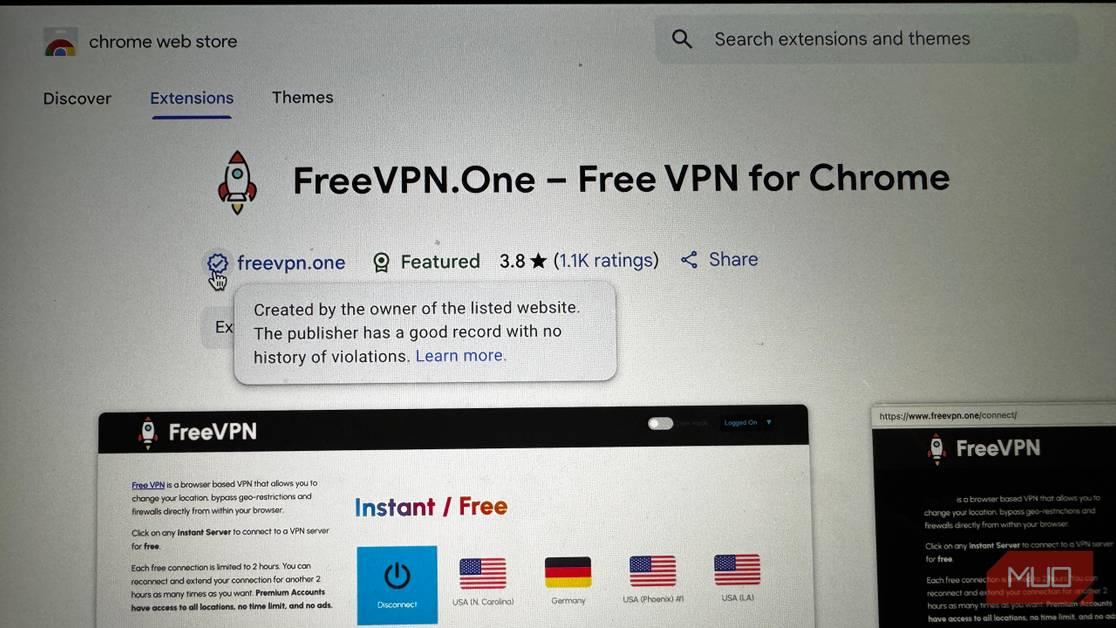
A popular VPN extension for Google Chrome has been screenshotting every page users visit -- FreeVPN.One flagged over enormous privacy concerns
Koi Security has revealed that a popular Google Chrome extension with more than 100,000 installs has been taking screenshots of every website its users visit and sending them to a domain controlled by the software's anonymous developer. The extension in question, FreeVPN.One, claims to be "the fastest free VPN for Chrome [sic]" and boasts a "Featured" badge that Google awards to extensions that "follow our technical best practices and meet a high standard of user experience and design." But it turns out FreeVPN.One has been undermining its users' privacy for months. "While VPN extensions legitimately need permissions like proxy and storage for core functionality," Koi Security said, "this one asks for more permissions that enable broad data collection." The company identified a trio of permissions -- tabs, and scripting -- that allow FreeVPN to inject a script into every website its users visit. "Seconds after any page loads, a background trigger grabs a screenshot and sends it to aitd[.]one/brange.php, bundled with the page URL, tab ID, and a unique user identifier," the report explains. "No user action, no UI hint, the screenshots are taken in the background without you ever knowing." FreeVPN.One's privacy policy does acknowledge that it can take screenshots of the pages its users visit, but it's only supposed to do so if users enable the so-called AI Threat Detection Feature, through which "a snapshot (screenshot) and related page information (such as the URL and visible page content) are transmitted from your browser to our secure servers and, if applicable, to our vetted analysis partners." That suggests FreeVPN.One only enables its data collection features if users opt-in to the AI Threat Detection Feature... but the developer says in another paragraph that they "use anonymized usage data to build our threat intelligence database, whether or not AI Protection is enabled," which aligns with Koi Security's findings. The policy has also changed recently. A copy of the policy from June 20 is missing the section about anonymized usage data, as well as the line "This system is in beta and provided 'as is' without warranties or guarantees of any kind, express or implied, including but not limited to accuracy, reliability, or fitness for a particular purpose." It's also missing the header stating that FreeVPN.One is operated by a company called CMO Ltd. There's no mention of who operates the extension at all; in fact, the only clue comes via the email Google provides for contacting the developer. The domain associated with that email redirects to a page for Phoenix Software Solutions with the URL "https://domain146.wixsite.com/phoenixsoftsol." Not exactly confidence-inspiring. Koi Security's report includes a breakdown of FreeVPN.One's slow transition from a seemingly innocuous VPN to a privacy-invading extension between April and July, as well as a summary of the company's interactions with the software's developer. (Who apparently stopped responding to the researchers' inquiries as soon as they asked for "evidence of legitimacy, such as a company profile, GitHub account, or LinkedIn page.") VPN providers often make ludicrous claims about the privacy and security benefits of using their services. It's worth remembering that using those services requires a significant amount of trust in the organizations providing them; such trust would almost certainly be better placed somewhere other than in a free Chrome extension operated by an unknown developer that screenshots every page its users visit.
[2]
Popular Chrome VPN extension caught secretly spying on users -- uninstall it right now
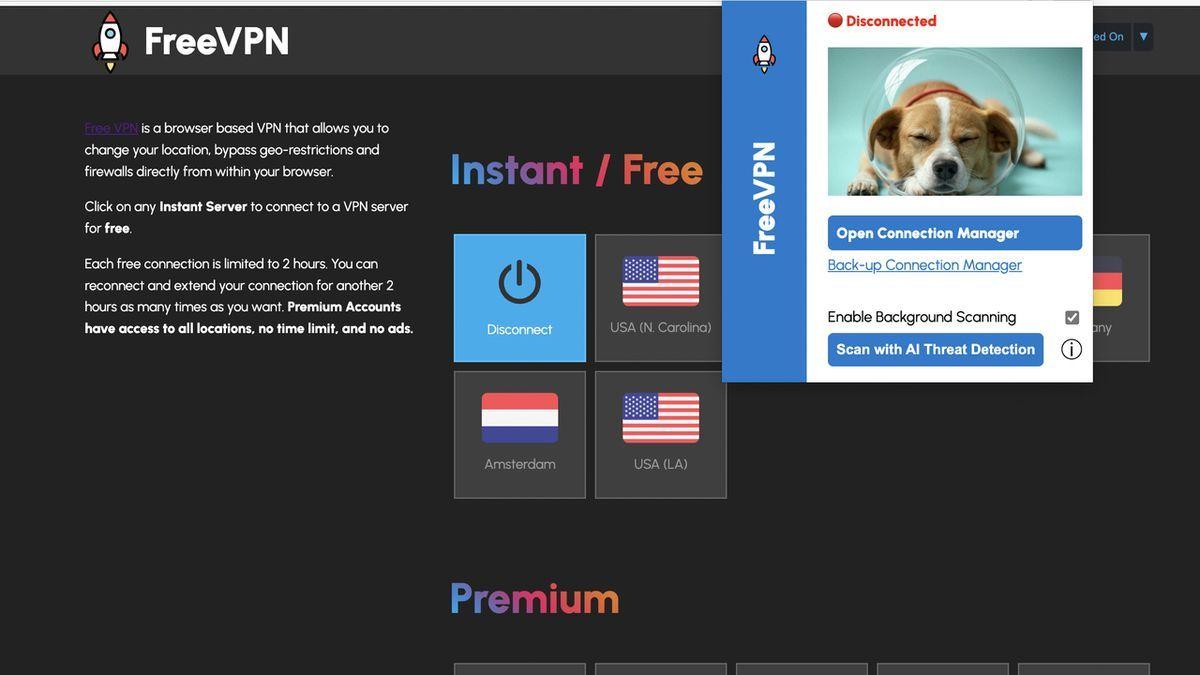
Extension was sneakily taking screenshots of user's displays without their knowledge A VPN is a common and recommended privacy tool when going online which is why many people download them as either apps for their computer or smartphone or as extensions for their browser of choice. However, not every VPN is trustworthy or even remains that way. Case in point, FreeVPN.One is a Chrome extension with 100,000 installs, a 3.8 star rating and even a verified badge. However, several recent updates have changed the status of the extension from safe to very suspicious. As reported by Cybernews, researchers at Koi Security recently put out a report detailing their findings on the extension complete with a timeline that showed how it has shifted to spying on its users instead of protecting their privacy. This was done by taking screenshots of their displays and sending this data back to remote servers. When a webpage is loading, the extension will grab a screenshot in the background and then send it back to a server with additional details like the URL, tab ID number and a unique user identifier. The report points out how screenshots can include sensitive and personal information like passwords, personal messages and banking details; sending these images to a third-party server is the exact opposite of what a privacy tool like a VPN is supposed to do for its users. Additionally, the extension now collects and transmits other sensitive information like IP geolocation, device information and sends it encoded in Base64, or via AES-256-GCM encryption with an RSA key which hides the data in transit. One of the features of the extension is "Scan with AI Threat Detection" which is intended to upload screenshots and URLs when the user clicks a 'check URL' button, however, there is no indication to the user that the extension has been repeatedly grabbing screenshots in the background even when this feature is not being used. These suspicious features were added recently and went live on July 17 of this year, which was right before strict age verification rules went into effect in the U.K.; many people in that area would be searching for VPNs after the rules went into place as a workaround. VPN extensions need some permissions to operate on a user's system - usually proxy and storage permissions. However, FreeVPN.One required suspiciously more access including all URLs, tabs and scripting permissions. The researchers at Koi Security pointed out that this, in addition to the other issues the extension exhibited, opened the door to persistent surveillance of its users. A developer is not named in either the privacy policy or the Terms of Service on the FreeVPN.One website, and their explanations to the security researchers about their findings do not match. According to the researchers: "The [developer] explained that the automatic screenshot capture is part of a Background Scanning feature, which should only trigger if a domain appears suspicious. In practice, we saw screenshots being captured on trusted services like Google Sheets and Google Photos, domains that cannot be considered suspicious" and the developer ceased communications when asked to provide proof of legitimacy. If you've installed this VPN extension, you should uninstall it and run a scan using one of the best antivirus software solutions. Likewise, you're going to want to check your browser extensions to ensure that it's removed and then check your screenshots folder as well.
[3]
If You Have This Chrome Extension Installed, You're Cooked
While they're useful, browser extensions can also require a lot of access to what you do in your browser. And if your worst nightmare is having a third-party tool take screenshots of your browsing and send them off to a third-party company, I have bad news for you. A "Featured" Chrome Extension Is Snooping on You Koi Security has published a report on how the Chrome extension FreeVPN.One extension abuses Chrome's extension permission system to take constant screenshots of your browsing. And this isn't some random extension that was uploaded last week and has no users. Its Chrome Web Store page boasts over 100,000 installs, a Featured badge, and a checkmark assuring that "The publisher has a good record with no history of violations". Once installed, this extension goes to work capturing data in the background without making you aware that it's doing this. Every time you load a page, it silently takes a screenshot while also capturing data about the page you're on, like the URL and any identifiers unique to you. It then ships this info off to a server that the extension developer controls. While it started as only a VPN, the extension has since added "AI Threat Detection" to its offering. This provides a page where you can paste any URL, and AI will (ostensibly) analyze whether it's safe. The privacy policy for this page does mention that it will upload a screenshot, but makes no mention of the screenshots being taken constantly in the background. The Monitoring Increased Over Time The Koi Security report explains how this didn't happen all at once. The FreeVPN.One extension has been around for a while, with reviews going back to at least 2020. However, the tracking behavior didn't start until April 2025. That's when the extension was updated to request access to all URLs you visit -- a far greater permission than a VPN should need. In June 2025, the extension received another update to include the mentioned "AI Threat Detection" tool, along with another permission to inject scripts. This scanner was likely added as a pretext for the screenshot capture and upload. Then, on July 17, 2025, the extension received another update with full spying capabilities. On July 25, another update added encryption of the exported data, making it harder to notice what was going on. The folks from Koi reached out to the developer, but his claims don't add up. He claimed that screenshots should only trigger on suspicious sites, but the Koi team saw screenshots captured on well-known domains like Google Photos. He stated that screenshots are not stored, but there's no way to prove this. And he stopped responding when they asked for proof that any of this was tied to a legitimate company. The developer's contact email on the Chrome extension page points to a generic Wix starter page. Avoid Dangerous Tools Spying on You We've seen many times how Chrome extensions can become a threat -- even those that were once legitimate. And while it's ridiculous that this spyware is currently "Featured" on the Chrome Web Store, there are lessons to take away that will help you avoid similar situations in the future. First, be vigilant about permissions when installing Chrome extensions. When you click Add to Chrome, you'll see a pop-up letting you know what permissions it requires. Think about what that extension might need to do the job it's promising. In this case, there's no need for a VPN to manage your extensions and change data on all websites. Second, it's always wise to do a quick scan of the material associated with apps or extensions you consider downloading. The Overview for this extension has numerous bits of awkward wording and poor grammar, including "chrome" and "ip" being lowercase. And its statement "Free VPN is unlimited and completely free for anyone to use" is a huge red flag. While legitimate free VPNs are fine to use, all VPNs need to make money somehow. No VPN provider can offer its services for free, forever. Like "lifetime" VPN offers, this is either a sign that the VPN provider is new and naïve, or that they have malicious intentions. The website for this VPN is also incredibly basic; you'd expect more than an amateurish design for something that's been around for years. While small-time developers aren't going to have impressive sites that rival major companies, they'll often at least have a GitHub page, a contact page, or something that shows they aren't developing in complete secrecy. Vet the browser extensions you use carefully, and don't trust random free VPNs that have no ties to real companies. There are enough well-known VPNs available that you should never open yourself to risk by installing one of these.
Share
Share
Copy Link
A widely-used Chrome VPN extension, FreeVPN.One, has been discovered to be secretly taking screenshots of users' browsing activities and sending them to remote servers, raising significant privacy concerns.
Chrome Extension Turns from VPN to Spyware
A popular Google Chrome extension, FreeVPN.One, with over 100,000 installs, has been caught secretly capturing screenshots of users' browsing activities and sending them to remote servers. This revelation, made by cybersecurity firm Koi Security, has raised significant privacy concerns and highlights the potential risks associated with browser extensions
1
.
Source: Tom's Guide
Gradual Transition to Spyware
The extension, which initially functioned as a legitimate VPN service, underwent a series of updates between April and July 2025 that gradually introduced invasive features:
- April 2025: Updated to request access to all URLs visited by users.
- June 2025: Added an "AI Threat Detection" tool and permission to inject scripts.
- July 17, 2025: Implemented full spying capabilities.
- July 25, 2025: Added encryption to exported data, making the spying harder to detect
3
.
Data Collection and Privacy Concerns
FreeVPN.One now collects and transmits sensitive information, including:
- Screenshots of every webpage visited
- URLs and tab IDs
- Unique user identifiers
- IP geolocation
- Device information
This data is sent to servers controlled by the extension's anonymous developer, encoded in Base64 or encrypted with AES-256-GCM and an RSA key
2
.Misleading Privacy Policy and Developer Claims
The extension's privacy policy acknowledges the ability to take screenshots, but only when users enable the "AI Threat Detection Feature." However, Koi Security's findings reveal that screenshots are taken regardless of this setting
1
.When confronted, the developer claimed that automatic screenshot capture should only trigger for suspicious domains. However, researchers observed screenshots being taken on trusted services like Google Sheets and Google Photos
2
.Chrome Web Store Verification and User Trust
Despite its invasive behavior, FreeVPN.One still displays a "Featured" badge on the Chrome Web Store, indicating that it "follow[s] our technical best practices and meets a high standard of user experience and design." This raises questions about the effectiveness of Google's vetting process for extensions
1
.
Source: MakeUseOf
Recommendations for Users
Security experts advise users to:
- Uninstall FreeVPN.One immediately if installed.
- Run a scan using reputable antivirus software.
- Be vigilant about permissions when installing Chrome extensions.
- Avoid free VPNs with no ties to legitimate companies.
- Carefully vet browser extensions before installation
2
3
.
Source: Tom's Hardware
This incident serves as a stark reminder of the potential risks associated with browser extensions and the importance of maintaining vigilance in online privacy and security practices.
References
Summarized by
Navi
[1]
[2]
Recent Highlights
1
OpenAI releases GPT-5.2 AI model after code red memo targets Google's Gemini 3 threat
Technology

2
Disney invests $1 billion in OpenAI, licenses 200+ characters for Sora video generator
Technology

3
Disney accuses Google of massive copyright infringement through AI-generated character images
Policy and Regulation




