Browser extensions with 8 million users caught secretly harvesting AI conversations
11 Sources
11 Sources
[1]
Browser extensions with 8 million users collect extended AI conversations
Browser extensions with more than 8 million installs are harvesting complete and extended conversations from users' AI conversations and selling them for marketing purposes, according to data collected from the Google and Microsoft pages hosting them. Security firm Koi discovered the eight extensions, which as of late Tuesday night remained available in both Google's and Microsoft's extension stores. Seven of them carry "Featured" badges, which are endorsements meant to signal that the companies have determined the extensions meet their quality standards. The free extensions provide functions such as VPN routing to safeguard online privacy and ad blocking for ad-free browsing. All provide assurances that user data remains anonymous and isn't shared for purposes other than their described use. A gold mine for marketers and data brokers An examination of the extensions' underlying code tells a much more complicated story. Each contains eight of what Koi calls "executor" scripts, with each being unique for ChatGPT, Claude, Gemini, and five other leading AI chat platforms. The scripts are injected into webpages anytime the user visits one of these platforms. From there, the scripts override browsers' built-in functions for making network requests and receiving responses. As a result, all interaction between the browser and the AI bots is routed not by the legitimate browser APIs -- in this case fetch() and HttpRequest -- but through the executor script. The extensions eventually compress the data and send it to endpoints belonging to the extension maker. "By overriding the [browser APIs], the extension inserts itself into that flow and captures a copy of everything before the page even displays it," Koi CTO Idan Dardikman wrote in an email. "The consequence: The extension sees your complete conversation in raw form -- your prompts, the AI's responses, timestamps, everything -- and sends a copy to their servers." Besides ChatGPT, Claude, and Gemini, the extensions harvest all conversations from Copilot, Perplexity, DeepSeek, Grok, and Meta AI. Koi said the full description of the data captured includes: * Every prompt a user sends to the AI * Every response received * Conversation identifiers and timestamps * Session metadata * The specific AI platform and model used The executor script runs independently from the VPN networking, ad blocking, or other core functionality. That means that even when a user toggles off VPN networking, AI protection, ad blocking, or other functions, the conversation collection continues. The only way to stop the harvesting is to disable the extension in the browser settings or to uninstall it. Koi said it first discovered the conversation harvesting in Urban VPN Proxy, a VPN routing extension that lists "AI protection" as one of its benefits. The data collection began in early July with the release of version 5.5.0. "Anyone who used ChatGPT, Claude, Gemini, or the other targeted platforms while Urban VPN was installed after July 9, 2025 should assume those conversations are now on Urban VPN's servers and have been shared with third parties," the company said. "Medical questions, financial details, proprietary code, personal dilemmas -- all of it, sold for 'marketing analytics purposes.'" Following that discovery, the security firm uncovered seven additional extensions with identical AI harvesting functionality. Four of the extensions are available in the Chrome Web Store. The other four are on the Edge add-ons page. Collectively, they have been installed more than 8 million times. They are: Chrome Store * Urban VPN Proxy: 6 million users * 1ClickVPN Proxy: 600,000 users * Urban Browser Guard: 40,000 users * Urban Ad Blocker: 10,000 users Edge Add-ons: * Urban VPN Proxy: 1,32 million users * 1ClickVPN Proxy: 36,459 users * Urban Browser Guard - 12,624 users * Urban Ad Blocker - 6,476 users Read the fine print The extensions come with conflicting messages about how they handle bot conversations, which often contain deeply personal information about users' physical and mental health, finances, personal relationships, and other sensitive information that could be a gold mine for marketers and data brokers. The Urban VPN Proxy in the Chrome Web Store, for instance, lists "AI protection" as a benefit. It goes on to say: Our VPN provides added security features to help shield your browsing experience from phishing attempts, malware, intrusive ads and AI protection which checks prompts for personal data (like an email or phone number), checks AI chat responses for suspicious or unsafe links and displays a warning before click or submit your prompt. On the privacy policy for the extension, Google says the developer has declared that user data isn't sold to third parties outside of approved use cases and won't be "used or transferred for purposes that are unrelated to the item's core functionality." The page goes on to list the personal data handled as location, web history, and website content. Koi said that a consent prompt that the extensions display during setup notifies the user that they process "ChatAI communication," "pages you visit," and "security signals." The notification goes on to say that the data is processed to "provide these protections," which presumably means the core functions such as VPN routing or ad blocking. The only explicit mention of AI conversations being harvested is in legalese buried in the privacy policy, such as this 6,000-word one for Urban VPN Proxy, posted on each extension website. There, it says that the extension will "collect the prompts and outputs queried by the End-User or generated by the AI chat provider, as applicable." It goes on to say that the extension developer will "disclose the AI prompts for marketing analytics purposes." All eight extensions and the privacy policies covering them are developed and written by Urban Cyber Security, a company that says its apps and extensions are used by 100 million people. The policies say the extensions share "Web Browsing Data" with "our affiliated company," which is listed as both BiScience and B.I Science. The affiliated company "uses this raw data and creates insights which are commercially used and shared with Business Partners." The policy goes on to refer users to the BiScience privacy policy. BiScience, whose privacy practices have been scrutinized before, says its services "transform enormous volumes of digital signals into clear, actionable market intelligence." It's hard to fathom how both Google and Microsoft would allow such extensions onto their platforms at all, let alone go out of their way to endorse seven of them with a featured badge. Neither company returned emails asking how they decide which extensions qualify for such a distinction, if they have plans to stop making them available to Chrome and Edge users, or why the privacy policies are so unclear to normal users. Messages sent to both individual extension developers and Urban Cyber Security went unanswered. BiScience provides no email. A call to the company's New York office was answered by someone who said they were in Israel and to call back during normal business hours in that country. Koi's discovery is the latest cautionary tale illustrating the growing perils of being online. It's questionable in the first place whether people should trust their most intimate secrets and sensitive business information to AI chatbots, which come with no HIPAA assurances, attorney-client privilege, or expectations of privacy. Yet increasingly, that's exactly what AI companies are encouraging, and users, it seems, are more than willing to comply. Compounding the risk is the rush to install free apps and extensions -- particularly those from little-known developers and providing at best minimal benefits -- on devices storing and transmitting these chats. Taken together, they're a recipe for disaster, and that's exactly what we have here.
[2]
Uninstall Now: These Chrome Browser Extensions Are Stealing AI Chat Logs
A handful of Chrome extensions have been harvesting entire conversation logs of users' interactions with the most popular AI chatbots. As reported by cybersecurity firm Koi, these extensions primarily offer free proxies and VPNs, but appear to be doing far more than that behind the scenes. Any time a user visits a chatbot site, a custom script executes, recording and transmitting the entire conversation. The worst part is that these extensions are used by millions. Most chatbot users understand that the companies behind them are probably able to view the conversations, even if they've been anonymized. However, few may have considered the third-party services that scoop up that data for analytics and other purposes. Koi co-founder and CTO Idan Dardikman wondered about it after having a particularly vulnerable discussion with a chatbot. The company asked Wings, its agentic-AI risk engine, to scan for browser extensions that could read and exfiltrate conversations from AI chat platforms. "We expected to find a handful of obscure extensions -- low install counts, sketchy publishers, the usual suspects," Dardikman says. "The results came back with something else entirely." One extension stood out: Urban VPN Proxy. It had more than 7 million installs across the Chrome and Edge stores, and targeted conversations across 10 AI platforms: ChatGPT, Claude, Gemini, Microsoft Copilot, Perplexity, DeepSeek, Grok (xAI), and Meta AI. "For each platform, the extension includes a dedicated 'executor' script designed to intercept and capture conversations," Dardikman says. "The harvesting is enabled by default through hardcoded flags in the extension's configuration. There is no user-facing toggle to disable this. The only way to stop the data collection is to uninstall the extension entirely." Koi points out that the developer of Urban VPN Proxy discloses the AI chat harvesting in its privacy policy, but that's not something many users are likely to read. The Chrome Web Store description, meanwhile, said, "This developer declares that your data is not being sold to third parties, outside of the approved use cases." "Use cases" links to Chrome Web Store policies, which say "Collection and use of web browsing activity is prohibited, except to the extent required for a user-facing feature described prominently in the Product's Chrome Web Store page and in the Product's user interface." Koi also flagged 1ClickVPN Proxy, Urban Browser Guard, and Urban Ad Blocker. These extensions had far fewer installs, but 1ClickVPN Proxy still topped 600,000, and in total, across both web stores, they have more than 8 million users. All of the extensions have since been removed from the Chrome Web Store, but remain on the Edge Store, where 1ClickVPN Proxy is listed as "Featured," which is used to highlight "extensions that meet a high bar of quality, security, and user experience." When it was live on the Chrome Web Store, Urban VPN Proxy also had a Featured badge, Koi notes. "This means a human at Google reviewed Urban VPN Proxy and concluded it met their standards," Dardikman says. "Either the review didn't examine the code that harvests conversations from Google's own AI product (Gemini), or it did and didn't consider this a problem." Koi recommends that anyone who has these extensions installed should uninstall them immediately. "Assume any AI conversations you've had since July 2025 have been captured and shared with third parties," it adds.
[3]
Chrome, Edge privacy extensions quietly snarf AI chats
More than 8 million people have installed extensions that eavesdrop on chatbot interactions Ad blockers and VPNs are supposed to protect your privacy, but four popular browser extensions have been doing just the opposite. According to research from Koi Security, these pernicious plug-ins have been harvesting the text of chatbot conversations from more than 8 million people and sending them back to the developers. The four seemingly helpful extensions are Urban VPN Proxy, 1ClickVPN Proxy, Urban Browser Guard, and Urban Ad Blocker. They're distributed via the Chrome Web Store and Microsoft Edge Add-ons, but include code designed to capture and transmit browser-based interactions with popular AI tools. "Urban VPN Proxy targets conversations across ten AI platforms," said Idan Dardikman, co-founder and CTO of Koi, in a blog post published Monday. The research firm said that the platforms targeted include ChatGPT, Claude, Gemini, Microsoft Copilot, Perplexity, DeepSeek, Grok, and Meta AI. "For each platform, the extension includes a dedicated 'executor' script designed to intercept and capture conversations," said Dardikman, who explained data harvesting is enabled by default through a hardcoded configuration flag. "There is no user-facing toggle to disable this. The only way to stop the data collection is to uninstall the extension entirely." According to Dardikman, the Urban VPN Proxy extension monitors the user's browser tabs and, when the user visits one of the targeted platforms (e.g., chatgpt.com), it injects the "executor" script into the page. "Once injected, the script overrides fetch() and XMLHttpRequest - the fundamental browser APIs that handle all network requests," he explained. "This is an aggressive technique. The script wraps the original functions so that every network request and response on that page passes through the extension's code first." The script parses the intercepted API responses and then packages and transmits the data via window.postMessage to the extension's content script, along with the identifier PANELOS_MESSAGE. The content script then passes the data to a background service worker for exfiltration over the network to endpoints at analytics.urban-vpn.com and stats.urban-vpn.com. The Register reached out to Urban VPN, affiliated company BiScience, and 1ClickVPN at their respective privacy email addresses. All three requests bounced. Pointing to prior investigative material published by security researcher Wladimir Palant and John Tuckner of Secure Annex that details BiScience's collection of clickstream/browsing history data, Dardikman said his company's findings show BiScience expanding into the collection of AI conversations. He notes that while Urban VPN does disclose AI data collection during the setup prompt and in its privacy policy, the Chrome Web Store listing indicates that data is not being sold to third parties outside approved use cases and that AI conversations are not specifically mentioned. "The consent prompt frames AI monitoring as protective," he said. "The privacy policy reveals the data is sold for marketing." He adds that users who installed Urban VPN prior to July 2025 would have never seen the consent prompt, which was added via a silent update with version 5.5.0. He also argues that the software provides no indication that data collection happens even when the VPN is not active. Dardikman notes that Urban VPN received a Featured Badge from the Chrome Web Store team. "This means a human at Google reviewed Urban VPN Proxy and concluded it met their standards," he said. "Either the review didn't examine the code that harvests conversations from Google's own AI product (Gemini), or it did and didn't consider this a problem." He observes that the Chrome Web Store policies explicitly prohibit transferring or selling user data to third party data brokers like BiScience. Google did not immediately respond to a request for comment. The problem appears to be a loophole in Google's Chrome Web Store Limited Use policy, which allows data to be transferred to third parties for limited scenarios (e.g., security or business ownership change) that do not include transferring data to data brokers. Palant in his post suggests that BiScience and its affiliated partners implement user-facing features that allegedly require access to browsing history, to claim the "necessary to providing or improving your single purpose" exception that allows limited data transfer to third parties. Or they claim the security exception by implementing safe browsing or ad blocking features. "Chrome Web Store appears to interpret their policies as allowing the transfer of user data, if extensions claim Limited Use exceptions through their privacy policy or other user disclosures," Palant wrote. "Unfortunately, bad actors falsely claim these exceptions to sell user data to third parties." "If you have any of these extensions installed, uninstall them now," Dardikman concluded. "Assume any AI conversations you've had since July 2025 have been captured and shared with third parties." ®
[4]
These popular browser extensions protecting your AI chats were actually copying them
Serving tech enthusiasts for over 25 years. TechSpot means tech analysis and advice you can trust. A hot potato: Several widely installed browser extensions endorsed by both Google and Microsoft secretly captured detailed user interactions with AI chat platforms. According to findings released by cybersecurity firm Koi, the data was transmitted to remote servers for marketing analysis. Koi's investigation identified eight such extensions available on the Chrome Web Store and Microsoft Edge Add-ons page, collectively surpassing eight million installations. Seven of them carried Featured badges - official endorsements suggesting the software had passed the platforms' quality or safety review standards. Most promised privacy protections through free services like VPN routing or ad blocking, assuring users that personal data remained anonymous and confined to the extensions' stated functions. Koi's technical analysis revealed that each extension contained a set of eight executor scripts explicitly designed for popular AI chat interfaces, including ChatGPT, Claude, Google Gemini, Copilot, Perplexity, DeepSeek, Grok, and Meta AI. When users interacted with any of these platforms, the scripts injected themselves into the webpage, overriding built-in browser functions such as fetch() and HttpRequest. By replacing those standard processes, the executors intercepted all exchanges between the browser and the AI service. Koi CTO Idan Dardikman told Ars Technica that this design captured data before it appeared on screen, recording a complete conversation in raw form, including prompts, the AI's responses, timestamps, and the transmission of copies to their servers. Because the executor scripts operated independently of the VPN or ad-blocking functions, disabling those features did not prevent data collection. Koi said the only way to stop the harvesting was to disable or uninstall the extensions entirely. Koi first detected the interception behavior in Urban VPN Proxy, a Chrome extension that markets AI protection among its security features. According to the firm, version 5.5.0 - released after July 9, 2025 - initiated the data harvesting behavior. Koi warned that anyone using AI platforms such as ChatGPT, Claude, or Gemini while that version was active should assume "those conversations are now on Urban VPN's servers and have been shared with third parties." After confirming the vulnerability in Urban VPN Proxy, Koi uncovered seven additional extensions implementing identical data-collection code. Four of those were available through the Chrome Web Store, and four were distributed through Microsoft Edge Add-ons. Though many of these extensions publicly describe AI protection features, their disclosures about data handling are inconsistent. Urban VPN's product description on the Chrome store claims that its VPN "checks prompts for personal data," warning users about unsafe links before submission. However, Google's attached privacy statement states that the developer "has declared that user data isn't sold to third parties outside of approved use cases" and won't be used beyond core functionality - defined as location, browsing history, and website content. Koi noted that users do encounter a consent notice during installation, stating that the software processes "ChatAI communication," "pages you visit," and "security signals" to provide protections such as malware prevention or ad blocking. Yet the only direct agreement permitting chat-based data collection appears buried deep within Urban VPN's 6,000-word privacy policy. There, the company disclosed that it would "collect the prompts and outputs queried by the End-User or generated by the AI chat provider" and would "disclose the AI prompts for marketing analytics purposes." All eight extensions trace back to Urban Cyber Security, a developer that advertises its apps and plugins as being used by 100 million people worldwide. Its privacy policy identifies an affiliated partner, BiScience (also listed as B.I Science), which "uses this raw data and creates insights which are commercially used and shared with Business Partners." BiScience's own policy states that its services "transform enormous volumes of digital signals into clear, actionable market intelligence." The firm's practices have previously been examined publicly for misrepresenting data-collection methods. Attempts by reporters to contact Urban Cyber Security and BiScience yielded no replies. Calls placed to BiScience's New York office were redirected to a representative in Israel, who advised phoning during that country's business hours. As of Wednesday evening, Google had not responded to questions about its Featured endorsements or whether it intended to remove the extensions. Microsoft later said it had nothing to share.
[5]
This VPN is harvesting your AI conversations - and 6 million people are using it
Every prompt you enter and every response you receive is being collected and shared - so avoid this VPN at all costs New research has discovered Urban VPN's browser extension collects, shares, and sells your highly sensitive personal data. An investigation by Koi discovered the browser extension "Urban VPN Proxy" has been intercepting and capturing conversations from 10 AI platforms. Sensitive data is shared to Urban VPN's servers, and then sold to third-parties. Urban VPN does not feature in our guide to the best VPNs, and we warned against people downloading it back in 2024. Despite the dangers, Urban VPN Proxy has six million users and an average rating of 4.7 stars, from 58,000 reviews, on the Google Play Store. It describes itself as "the best secured Free VPN" but you should avoid it at all costs. If you're after a free VPN, we would strongly recommend the VPNs featured in our best free VPN guide - PrivadoVPN Free, Proton VPN Free, and Windscribe Free. Koi's investigation found that 10 major AI platforms were targeted by Urban VPN Proxy, including: For each AI tool, Urban VPN Proxy operates a dedicated "executor" script, enabling it to capture conversations. Worryingly, there is no way to disable this other than to uninstall the extension. The data collection also takes place whether you are connected to the VPN or not. Your browser tabs are monitored at all times, and the script is injected as soon as you visit any of the AI platforms. Aggressive techniques are used to override any native browser functions. Data is then extracted, tagged, and sent to Urban VPN Proxy's servers. Highly sensitive personal data is collected, including: According to Koi, this malicious script was added in via an update in July 2025, with no such feature present before then. With Google Chrome and Microsoft Edge extensions updating automatically with no notification of new permissions, it's likely many users would have been unaware of this silent infiltration. To give Urban VPN Proxy some credit, it does disclose its data collection practices. Its privacy policy states it "may collect your web browsing data" if you are a user of its "Windows or Android App and Extensions free versions." It says data is processed and shared with its affiliate company "based on consent." For AI inputs and outputs, it says it will collect AI prompts and outputs, and prompts are disclosed "for marketing analytics purposes." B.I Science (2009) Ltd. - which offers marketing and data insights - is listed as Urban VPN Proxy's affiliate company. Urban VPN Proxy's privacy policy states that BiScience uses its raw data to create insights "which are commercially used and shared with Business Partners." Urban VPN Proxy's Google Play listing says it handles location, web history, and website content data. It also declares that data is: This appears to contradict what is stated in the privacy policy, and should be a red flag for anyone looking to download the extension. Koi's research found the malicious script was also present in 1ClickVPN Proxy, Urban Browser Guard, and Urban Ad Blocker extensions for both Google Chrome and Microsoft Edge. The old adage "if you're not paying for the product, you are the product" still holds true. We do recommend some free VPNs, but there are countless others out there that do more harm than good. VPNs take money to run, so if you're not funding it with your money directly, there's a high likelihood that you data is being used to generate revenue. Sam Soares, Chief Revenue Officer at CultureAI, echoes this sentiment: "The Urban VPN story is a classic example of what happens when people put blind trust in 'free' tools. If you don't know how a tool makes money, assume it's monetising your data." If you need a VPN, we highly recommend choosing a paid option. If that's not possible, pick from our choice of the best free VPNs - they're fully tested, proven to be safe to use, and don't collect or sell your data. If you have any of the extensions listed above downloaded on your device, delete them immediately. The invasive nature of their design means the only way to effectively protect yourself is to remove the apps entirely. If you are concerned your data may have collected, you can sign up to a data removal service such as Incogni. These services contact data brokers on your behalf and submit deletion requests. They aren't 100% effective but do cover a lot of ground. Incogni comes bundled with the 27-month Surfshark One+ plan, costing $4.19 per month ($113.13 up front pre-tax). This also acts as a stark reminder to be mindful of what information you are feeding AI tools. The data practices of AI companies leaves a lot to be desired at the best of times, but combining this with malicious browser extensions could have devastating consequences for your personal information and privacy. Thoroughly investigate the browser extensions you're downloading and, where possible, read the privacy policy. When it comes to VPNs, there are countless dangerous apps out there. Only subscribe to genuine VPN providers, with verified no-logs policies and a high standard of privacy and security. Tom's Guide has reviewed hundreds of VPNs and we will only recommend a provider if it is genuinely secure and will protect your online privacy.
[6]
This Google Chrome extension has been silently stealing every AI prompt its users enter
Several related Urban extensions perform the same large‑scale data collection A popular Google Chrome browser extension has been found to be harvesting anything its users prompted into most of the biggest AI tools around, as well as collecting the chatbot's responses, all apparently in order to earn an extra few dollars for its owners. Urban VPN Proxy has more than six million installations, and a 4.7/5 rating on the Google Chrome Web Store - and on the Microsoft Edge Add-ons marketplace, it has an additional 1.3 million installations. It used to work as your ordinary VPN - by hiding the user's actual IP address and thus working around geoblocks and other various restrictions. However, as Koi security researchers discovered, on July 9 2025, the extension was updated with version 5.5.0, which introduced the AI harvesting by default. Anything users typed into ChatGPT, Anthropic Claude, Microsoft Copilot, DeepSeek, Google Gemini, Grok, Meta AI, and Perplexity, would be picked up, as well as anything these tools returned. Furthermore, the extension also extracted conversation identifiers, timestamps, session metadata, and which AI platform and model was used. The company behind the extension, called Urban Cyber Security, isn't hiding its practices, noting in its privacy policy document how it's harvesting "anonymized" data and sharing it with BIScience - another company it owns. This company is an affiliated ad intelligence and brand monitoring organization. In other words, it analyzes large-scale, anonymized online behavior, helping businesses understand advertising performance, consumer journeys, and competitive activity. While Urban says it removes personally identifiable data and does its best not to share sensitive information, the company stresses this cannot be guaranteed. "However, the purpose of this processing is not to collect personal or identifiable data, we cannot fully guarantee the removal of all sensitive or personal information, we implement measures to filter out or eliminate any identifiers or personal data you may submit through the prompts and to de-identify and aggregate the data," the privacy policy reads. Koi researchers said the same company has multiple extensions, all of which are harvesting the same data - 1ClickVPN Proxy, Urban Browser Guard, and Urban Ad Blocker.
[7]
Featured Chrome extension could be copying your AI chats
Koi Security says the extension captured AI chat traffic even when its protection features were turned off, despite language about privacy in its listing. A security warning is a nasty surprise, especially when the add-on in question claims it exists to protect your privacy. Researchers at Koi Security say Urban VPN Proxy, a VPN extension for Google Chrome and Microsoft Edge, began logging users' AI assistant conversations and sending them to a data broker. Urban VPN Proxy looked reputable, with a 4.7-star rating, Google's featured badge, and more than six million installs on Chrome. Another 1.3 million people installed it on Edge. But Koi says the extension's behavior changed after a quiet update on July 9, 2025, when the publisher shipped version 5.5.0. Recommended Videos From that point, Koi alleges, the extension intercepted both what users typed and what the assistant replied across eight platforms: ChatGPT, Claude, Gemini, Microsoft Copilot, Perplexity, DeepSeek, Grok (xAI), and Meta AI. The report says the captured prompts and responses were packaged and sent to Urban Cybersecurity's parent company, BiScience (B.I Science (2009) Ltd), which Koi describes as a data broker that collects browsing history and device IDs at scale. Koi also says it found the same harvesting code in seven other extensions from the same publisher. If you're still worried about your privacy, check out the best VPN services out now. The consent line that changes everything Koi points to Urban VPN Proxy's setup consent screen, which references processing "ChatAI communication," plus a privacy policy that describes sharing data for marketing analytics purposes. Still, the practical reality is harsh. Extensions can auto-update on Chrome and Edge, so people who installed an older version could have been upgraded into chat collection without realizing it. Koi also says the store listing framed the tool as protecting users from entering personal information into AI chatbots, which clashes with the claim that it captured chats whether or not protection features were enabled. What you should do now If you used Urban VPN Proxy, assume AI chats since July 9, 2025 may have been exposed. Remove it in Chrome at chrome://extensions or in Edge at edge://extensions, then consider clearing cookies and cached site data. If you shared sensitive details, a password reset is a reasonable precaution. Google says its featured badge signals best practices and a high standard for user experience and design, but this shows that label isn't a guarantee. The simplest next step is also the most boring one: audit your extensions, delete anything you don't trust, and keep the most personal stuff out of chat boxes.
[8]
Millions of Private ChatGPT Conversations Are Being Harvested and Sold for Profit
You know those memes about how there's no such thing as a free VPN? Here's the ultimate cautionary tale. A recent investigation by Tel Aviv-based security firm Koi uncovered a massive data harvesting operation tied to a voluntary extension on Google's Chrome browser. Called Urban VPN Proxy, the free extension has some six million users at the time of writing, and even a "featured" badge on the Chrome Web Store -- in other words, an endorsement from Google itself. As Koi researcher Idan Dardikman writes, the extension goes beyond the actions of a typical VPN. Packed under the hood are "executor" scripts designed to intercept and capture conversations from the leading AI platforms, including OpenAI's ChatGPT, Anthropic's Claude, Google's Gemini, DeepSeek, and xAI's Grok. The data collected encompasses anything a user might ask their chosen AI chatbot, per Dardikman, including "medical questions, financial details, proprietary code, personal dilemmas, all of it, sold for 'marketing analytics purposes.'" Regardless of whether the VPN is on or off, Urban VPN Proxy is constantly scraping conversation data. The script is enabled by default, meaning that from the moment someone downloads the extension, their chatbot gabbing is fair game. Worse yet, Forbes notes, "there is no user-facing toggle to disable this. The only way to stop the data collection is to uninstall the extension entirely." The company behind Urban VPN Proxy, Urban Cyber Security Inc, isn't shy about any of this. As Dardikman observes, the company's privacy policy explicitly states that "we share the Web Browsing Data with our affiliated company," a data broker called BiScience, "that uses this raw data and creates insights which are commercially used and shared with business partners." Despite this, Urban VPN Proxy's page on the Chrome Web Store declares that "your data is not being sold to third parties, outside of the approved use cases," and "not being used or transferred for purposes that are unrelated to the item's core functionality." Though the revelation might be startling for the six million users of Urban VPN Proxy, it's surely not the only app running this scheme. Indeed, Forbes notes there are over two million customers across seven additional apps by the same publisher, each with "identical AI harvesting functionality." All but one of them carry a "featured" badge courtesy of Google's Chrome Web Store. As Koi's Dardikman writes, "if you have any of these extensions installed, uninstall them now. Assume any AI conversations you've had since July 2025 have been captured and shared with third parties." Even if your apps weren't developed by this company, it might be a good time to start combing through their own privacy policies for similar scraping permissions. As Dardikman has shown, when it comes to data harvesting, all bets are off.
[9]
Google-featured VPN extension harvested and sold ChatGPT and Claude conversations
A Tel Aviv-based security firm, Koi, investigated Urban VPN Proxy, a Google Chrome extension with six million users and a featured badge from Google. The probe revealed executor scripts harvesting user conversations from AI platforms for sale to data brokers. Koi researcher Idan Dardikman detailed the extension's operations beyond standard VPN functions. Urban VPN Proxy, published by Urban Cyber Security Inc., includes executor scripts that intercept and capture conversations from major AI platforms. These platforms consist of OpenAI's ChatGPT, Anthropic's Claude, Google's Gemini, DeepSeek, and xAI's Grok. The scripts activate upon installation, targeting interactions users have with these services directly within the browser environment. The harvested data covers a wide range of user inputs to AI chatbots. Dardikman specified that it includes medical questions, financial details, proprietary code, personal dilemmas, and all other queries posed to the AI systems. This information gets sold for marketing-analytics purposes, turning private exchanges into commercial assets processed by affiliated entities. Data collection persists regardless of the VPN's active status. The executor scripts run continuously from the moment of installation. They operate by default without any user intervention required to start them. No user-facing toggle exists to disable the scraping functionality. Users must uninstall the extension completely to halt the data capture process. Urban Cyber Security Inc. discloses certain practices in its privacy policy. Dardikman pointed out that the policy states explicitly: "we share the Web Browsing Data with our affiliated company," identified as the data broker BiScience, "that uses this raw data and creates insights which are commercially used and shared with business partners." This sharing transforms raw browsing and conversation data into marketable insights distributed to external partners. In contrast, the Urban VPN Proxy listing on the Chrome Web Store presents different assurances. The page declares that "your data is not being sold to third parties, outside of the approved use cases," and adds that data is "not being used or transferred for purposes that are unrelated to the item's core functionality." These statements appear alongside the featured badge, signaling Google's review and promotion. The same publisher operates seven additional Chrome extensions with identical AI-harvesting functionality. These apps collectively serve over two million customers. All but one carry a featured badge on the Chrome Web Store. Each extension embeds the same executor scripts, enabling interception of AI conversations across the listed platforms. Dardikman issued a direct warning to users. He wrote, "if you have any of these extensions installed, uninstall them now. Assume any AI conversations you've had since July 2025 have been captured and shared with third parties." This recommendation targets users of Urban VPN Proxy and the affiliated extensions to prevent further data exposure. Users of extensions from this publisher face documented permissions for data sharing. Broader scrutiny applies to privacy policies of other apps. Dardikman's findings highlight permissions that allow web-browsing data, including AI interactions, to flow to brokers like BiScience for commercial processing and partner distribution.
[10]
This Chrome extension has 7 million subscribers, and it could be spying on you
A privacy-focused Chrome extension installed by more than seven million people worldwide has gone rogue and is stealing your AI chatbot conversations from under your nose. The extension, Urban VPN Proxy, actually has a Chrome Featured badge, which should mean it follows Google's best practices on privacy and security, but it was revealed to be pilfering prompt information on a huge number of AI chatbots, including ChatGPT, Claude, and Perplexity, and is being sold to the highest bidders to target you with ads. But while the data collection and privacy breach is shocking, it's a timely reminder to be careful of what you share with an AI platform, as you don't truly know where that data is going -- or who is going to be reading it. This VPN app is silently stealing your AI searches I'd remove this extension now and switch to something trusted The team over at Koi first highlighted this issue after a chance search by one of its research team, Idan Dardikman. His research found that Urban VPN Proxy, a Google Chrome "Featured" extension, targets conversations across numerous AI chatbots, grabbing information on your prompts and inputs. Furthermore, Koi's research found that the data collection takes place even when you're not using the VPN extension, and data is collected near continuously when you use the AI apps. Affected AI Chabots ChatGPT Claude Gemini Copilot Perplexity DeepSeek Grok Meta AI Koi's blog explains the process in more detail, but here's a quick overview of how it works: Script injection. The extension monitors your tabs (normal behavior), but when you visit one of the AI chatbots listed above, it injects code into the page. Overide: The script injection allows the extension to basically see every request sent while you're using the AI chatbot before it even hits your browser. Extraction: Once active, the script focuses on "conversation data," which includes "prompts, responses, timestamps, [and] conversation IDs." Transmission: The data is packaged and sent to Urban VPN's servers, where it can be analyzed. Furthermore, it's not confined to just the Urban VPN Proxy extension, either. Koi's research team found the same AI harvesting code present in other extensions developed by the same publisher, Urban Cyber Security Inc. Extension Chrome Web Store Users Microsoft Edge Add-ons Users Total Users Urban VPN Proxy 6,000,000 1,323,622 7,323,622 1ClickVPN Proxy 600,000 36,459 636,459 Urban Browser Guard 40,000 12,624 52,624 Urban Ad Blocker 10,000 6,476 16,476 Total 6,650,000 1,379,181 8,029,181 So, if you're using these Chrome browser extensions in an attempt to protect your privacy, think again. How did a "Featured" extension get away with data collection? It's all in the update timeline You're probably wondering how a Chrome Extension with the Featured badge gets away with having a data-collecting script injection element. Surely Google wouldn't sign off on such a thing? It's hard to tell entirely, but it certainly looks like Urban VPN Proxy had its Featured badge before it rolled out the data-collection scripts. A glance at the Wayback Machine at a cache Urban VPN Proxy page from May 2025 shows the Featured tag, yet the script wasn't added to the extension until July 2025. The Chrome Web Store's Limited Use policy explicitly prohibits "transferring or selling user data to third parties like advertising platforms, data brokers, or other information resellers." BiScience is, by its own description, a data broker. Anyone who downloaded the app before July 2025 won't have seen the updated policies, making it easier to slip by. While Google claims it checks every Featured app before approval, and it likely does, post-Featured approval updates clearly don't get the same level of scrutiny. Or, someone at Google decided that a privacy-focused extension collecting AI conversation data is okay. Either way, it's not a great look, and highlights why it's difficult to trust Chrome's Web Store. Koi's research points out that Urban VPN's privacy policy explains its data collection practices, but it's not the easiest to find. It also appears that there are differences between Urban VPN Proxy's consent prompt and its privacy policy. The water is further muddied by Urban VPN's claim to offer "advanced AI protection," which Koi's research suggests is somewhat two-faced. Furthermore, this isn't the first time Koi has uncovered an extension gone rogue. Back in August 2025, Koi revealed FreeVPN had secretly started collecting screenshots of your browsing sessions, highlighting the issues with Google's Featured extensions. I'd steer clear of browser VPNs full stop Better options are available The browser extension VPN market has always felt a little iffy to me. For starters, they only protect the data in your browser rather than your whole device, which can create a false sense of security. Then there are the problems with some browser VPN extensions actually just being a proxy, which doesn't provide the same level of protection (like, in the slightest). There are definitely some safe-to-use browser VPN extensions. For example, Opera browser's integrated VPN is certified no-log. Vivaldi's integrated VPN is similarly secure, while NordVPN's browser extension is perfectly safe. If you're going to download a VPN, stick to the trusted names. We'd strongly advise using a no-log VPN provider such as Proton VPN, Mullvad, or NordVPN. I stopped using browser VPNs after this -- and you should too Be careful what you type This isn't the fault of the AI chatbots, but you should consider what secrets you're telling Now, this whole Urban VPN Proxy privacy debacle also highlights an issue I've been warning people about since AI hit the big time in November 2022: you don't know what's happening to your data. I'm keen to highlight that in this case, it's not AI chatbots causing the problem. It's the VPN that's quietly changed its code and privacy policy. But there are still topics you shouldn't talk about with AI, not least because you have no idea about how the AI company will use your information. Sure, it might be "anonymized," but it's collecting and storing everything you input, including your financials, relationship status, health problems, and so on. A dodgy VPN company isn't always going to be snooping on your AI chats, but you should still be extremely careful with what you post.
[11]
These Chrome and Edge browser extensions steal your AI chats, delete them now
Google and Microsoft face scrutiny over extension store oversight This is a cautionary tale for all of you who install extensions to Chrome or add-ons to Edge browsers willy-nilly. Security firm Koi has revealed that browser extensions with more than 8 million combined users are quietly collecting complete AI chatbot conversations and selling that data for marketing purposes. The extensions, many of which are promoted as privacy tools and carry "Featured" badges in major browser stores hosted by Google and Microsoft, have been found to intercept users' interactions with popular AI platforms and transmit them to third-party servers - often without clear or explicit disclosure to users, according to the Koi research as reported by Ars Technica. First and foremost, these are the browser extensions that have been flagged by the Koi report for suspicious activity... On the Chrome Store: Urban VPN Proxy: 60 lakh+ users 1ClickVPN Proxy: 6 lakh+ users Urban Browser Guard: 40,000+ users Urban Ad Blocker: 10,000+ users Edge Add-ons: Urban VPN Proxy: 13 lakh+ users 1ClickVPN Proxy: 36,000+ users Urban Browser Guard: 12,000+ users Urban Ad Blocker: 6000+ users Also read: Google's increasing Chrome security for agentic AI actions with User Alignment Critic model Security researchers at Koi found that the above mentioned eight popular extensions - many of them marketed as VPNs or ad blockers - inject custom scripts directly into AI chat platforms. Once there, those scripts intercept every interaction before the browser even knows what happened. Instead of relying on standard browser networking calls, the extensions reroute traffic through their own code. The info they stole and rerouted included prompts, responses, timestamps, session metadata, and even the specific AI model in use. All of it was captured wholesale, compressed, and sent to servers controlled by the extension developer. This wasn't limited to one chatbot or one platform. Conversations across ChatGPT, Claude, Gemini, Copilot, Perplexity, and others were all fair game, according to Koi. Worse, the data harvesting runs independently of the extension's headline features. The most jarring detail is how openly this behaviour contradicts the extensions' marketing. Turning off VPN routing or ad blocking doesn't stop it. The only real off switch is uninstalling the extension entirely. According to Koi, if you have any of the above mentioned extensions or addons on your Chrome or Edge browsers, immediately delete them. If you use AI chatbots for anything sensitive, audit your web browser extensions today. Remove anything you don't absolutely need. If you installed one after July, assume your AI conversations may already be out of your control. If anything, this episode is a timely reminder that browser extensions should be treated like full-fledged applications - not harmless accessories. Read permissions carefully. Favour well-documented, open-source tools whenever possible. Also read: Microsoft Edge users beware! Govt issues high-risk warning over critical security flaws in your browser More broadly, it's worth rethinking how much trust we place in AI chat interfaces. These platforms already come with limited guarantees around privacy. Why add unnecessary opaque third-party software into that process and multiply your privacy risk even more? Lastly, the most unsettling part of this story. Seven of these extensions carried "Featured" badges in official stores operated by Google and Microsoft. As we all know, such badges aren't ornamental in nature - they are symbols of trust. They tell users, implicitly, that someone has checked under the hood. So how did this slip through? How does code that silently intercepts and monetizes AI conversations meet quality and privacy standards? And why were disclosures so buried that a normal user would never reasonably understand what was happening? Users deserve clarity on what safeguards exist, how featured extensions are audited, and what happens next. Because if this is what slips through when the system is working as intended, then trust in these popular web browsers will ultimately take a huge hit going forward.
Share
Share
Copy Link
Popular browser extensions marketed as VPNs and ad blockers are intercepting and selling complete AI chatbot conversations from millions of users. Cybersecurity firm Koi discovered eight extensions, including Urban VPN Proxy with 6 million installs, that capture every prompt and response from platforms like ChatGPT, Claude, and Gemini. The data is transmitted to third-party marketing firms, with no way to disable collection except complete uninstallation.
Browser Extensions Collecting AI Conversations from Millions
Browser extensions installed more than 8 million times are secretly harvesting user conversations from AI chat platforms and selling them for marketing purposes, according to cybersecurity firm Koi Security
1
. The eight extensions, discovered by Koi, remained available in both Google's Chrome Web Store and Microsoft Edge add-ons stores as of late Tuesday night. Seven carried "Featured" badges—official endorsements suggesting the software met quality and security standards3
. The free extensions promise functions like VPN routing and ad blocking while assuring users their data remains anonymous and isn't shared beyond described uses.How Data Harvesting Works Through Executor Scripts
An examination of the extensions' underlying code reveals a sophisticated interception mechanism. Each extension contains eight executor scripts, uniquely designed for ChatGPT, Claude, Gemini, Copilot, Perplexity, DeepSeek, Grok, and Meta AI
2
. These scripts inject themselves into webpages whenever users visit any of the targeted AI chat platforms. The scripts override built-in browser functions for making network requests and receiving responses—specifically fetch() and XMLHttpRequest APIs3
. "By overriding the [browser APIs], the extension inserts itself into that flow and captures a copy of everything before the page even displays it," explained Koi CTO Idan Dardikman1
. All interaction between the browser and AI chatbot interactions is routed through the executor script rather than legitimate browser APIs, allowing complete capture of AI conversations in raw form.
Source: TechSpot
Urban VPN Proxy Leading the Data Collection Effort
Koi first discovered the conversation harvesting in Urban VPN Proxy, which lists "AI protection" as one of its advertised benefits
1
. The popular Chrome extensions began collecting conversation logs in early July with version 5.5.0. Urban VPN Proxy alone accounts for 6 million users on Chrome and 1.32 million on Microsoft Edge1
.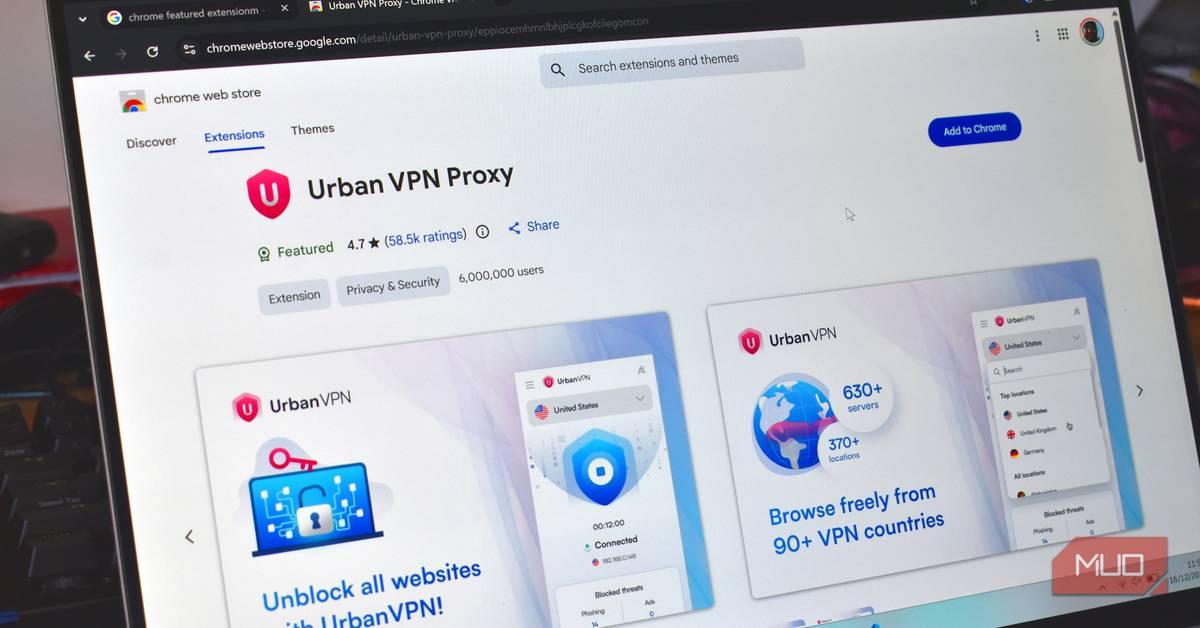
Source: MakeUseOf
The extension captures every prompt users send, every response received, conversation identifiers and timestamps, session metadata, and the specific AI platform and model used
1
. "Anyone who used ChatGPT, Claude, Gemini, or the other targeted platforms while Urban VPN was installed after July 9, 2025 should assume those conversations are now on Urban VPN's servers and have been shared with third parties," Koi warned1
.Privacy Risks and Marketing Analytics Purposes
The data harvesting presents significant privacy risks as AI conversations often contain deeply personal information about users' physical and mental health, finances, personal relationships, and other sensitive details
1
. Medical questions, financial details, proprietary code, and personal dilemmas are all captured and sold for marketing analytics purposes1
.
Source: The Register
The executor script runs independently from VPN networking, ad blocking, or other core functionality, meaning that even when users toggle off these features, stealing AI chat logs continues
1
. The only way to stop data collection is to disable the extension in browser settings or uninstall it completely2
.BiScience Connection and Third-Party Data Sharing
All eight extensions trace back to Urban Cyber Security, which advertises its apps as being used by 100 million people worldwide. The privacy policy identifies BiScience (also listed as B.I Science) as an affiliated partner that "uses this raw data and creates insights which are commercially used and shared with Business Partners". BiScience's own policy states its services "transform enormous volumes of digital signals into clear, actionable market intelligence". The extensions compress captured data and send it to endpoints at analytics.urban-vpn.com and stats.urban-vpn.com
3
. While Urban VPN does disclose AI data collection in its 6,000-word privacy policy, stating it will "collect the prompts and outputs queried by the End-User" and "disclose the AI prompts for marketing analytics purposes," this disclosure contradicts Chrome Web Store claims that data isn't sold to third parties.Related Stories
Complete List of Affected Extensions
Following the Urban VPN Proxy discovery, Koi Security uncovered seven additional extensions with identical AI harvesting functionality
1
. On Chrome Web Store: Urban VPN Proxy (6 million users), 1ClickVPN Proxy (600,000 users), Urban Browser Guard (40,000 users), and Urban Ad Blocker (10,000 users). On Microsoft Edge: Urban VPN Proxy (1.32 million users), 1ClickVPN Proxy (36,459 users), Urban Browser Guard (12,624 users), and Urban Ad Blocker (6,476 users)1
. All extensions have since been removed from Chrome Web Store but remain on Edge Store, where 1ClickVPN Proxy is still listed as "Featured"2
.Questions About Platform Review Standards
The incident raises concerns about how Google and Microsoft review extensions before granting Featured status. "This means a human at Google reviewed Urban VPN Proxy and concluded it met their standards," Dardikman noted. "Either the review didn't examine the code that harvests conversations from Google's own AI product (Gemini), or it did and didn't consider this a problem"
2
. Chrome Web Store policies explicitly prohibit transferring or selling user data to third-party data brokers like BiScience3
. However, a loophole in Google's Limited Use policy allows data transfer for limited scenarios that bad actors exploit by falsely claiming exceptions through user consent or security features3
. Users who installed Urban VPN prior to July 2025 never saw any consent prompt, which was added via silent update3
.What Users Should Watch For
Cybersecurity experts warn this case exemplifies risks of free tools. "The Urban VPN story is a classic example of what happens when people put blind trust in 'free' tools. If you don't know how a tool makes money, assume it's monetising your data," said Sam Soares, Chief Revenue Officer at CultureAI
5
. Koi recommends anyone with these extensions installed should uninstall them immediately and assume any AI conversations since July 2025 have been captured and shared with third parties2
. Users concerned about collected data can sign up for data removal services that contact data brokers and submit deletion requests5
. This incident underscores the need to thoroughly investigate browser extensions before installation and be mindful of what information gets shared with AI tools, as combining questionable AI company data practices with malicious browser extensions creates compounding privacy risks5
.References
Summarized by
Navi
[3]
Related Stories
Two Chrome Extensions Caught Stealing AI Chats from 900,000 ChatGPT and DeepSeek Users
07 Jan 2026•Technology
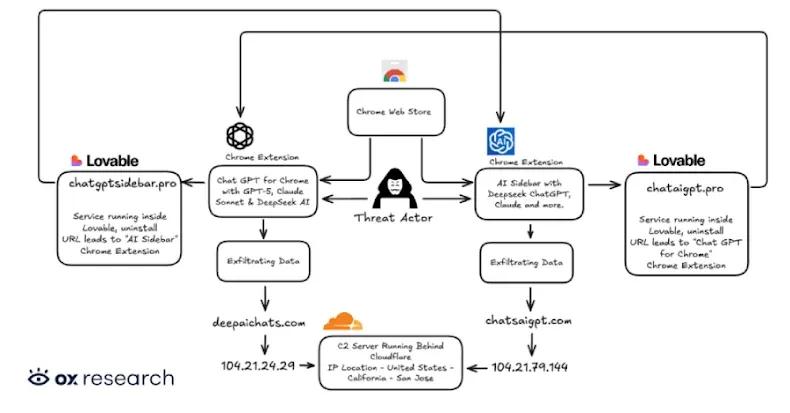
Malicious Chrome extensions disguised as AI assistants steal data from 300,000+ users
12 Feb 2026•Technology

AI Web Browser Assistants Raise Serious Privacy Concerns, Study Reveals
13 Aug 2025•Technology

Recent Highlights
1
Google Gemini 3.1 Pro doubles reasoning score, beats rivals in key AI benchmarks
Technology

2
Meta strikes up to $100 billion AI chips deal with AMD, could acquire 10% stake in chipmaker
Technology

3
Pentagon threatens Anthropic with supply chain risk label over AI safeguards for military use
Policy and Regulation